
Uranium Finance, an automated market maker platform on the Binance Smart Chain, has reported a security incident that resulted in a loss of about $50 million.
Tweeting on Wednesday, Uranium revealed that the exploit targeted its v2.1 token migration event and that the team was in contact with the Binance security team to mitigate the situation.
(1/2)‼️ Uranium migration has been exploited, the following address has 50m in it The only thing that matters is keeping the funds on BSC, everyone please start tweeting this address to Binance immediately asking them to stop transfers.
— Uranium Finance (@UraniumFinance) April 28, 2021
The hacker reportedly took advantage of bugs in Uranium’s balance modifier logic that inflated the project’s balance by a factor of 100.
This error reportedly allowed the attacker to steal $50 million from the project. As of the time of writing, the contract created by the hacker still holds $36.8 million in Binance Coin (BNB) and Binance USD (BUSD).
The remaining stolen funds include 80 Bitcoin (BTC), 1,800 Ether (ETH), 26,500 Polkadot (DOT), 5.7 million Tether (USDT), as well as 638,000 Cardano (ADA) and 112,000 u92, the project's native coin.
Details from BscScan show the attacker swapping the ADA and DOT tokens for ETH, upping the Ether stash to about 2,400 ETH.
Meanwhile, the alleged mastermind of the theft has already moved 2,400 ETH, worth about $5.7 million, using the Ethereum privacy tool Tornado Cash.
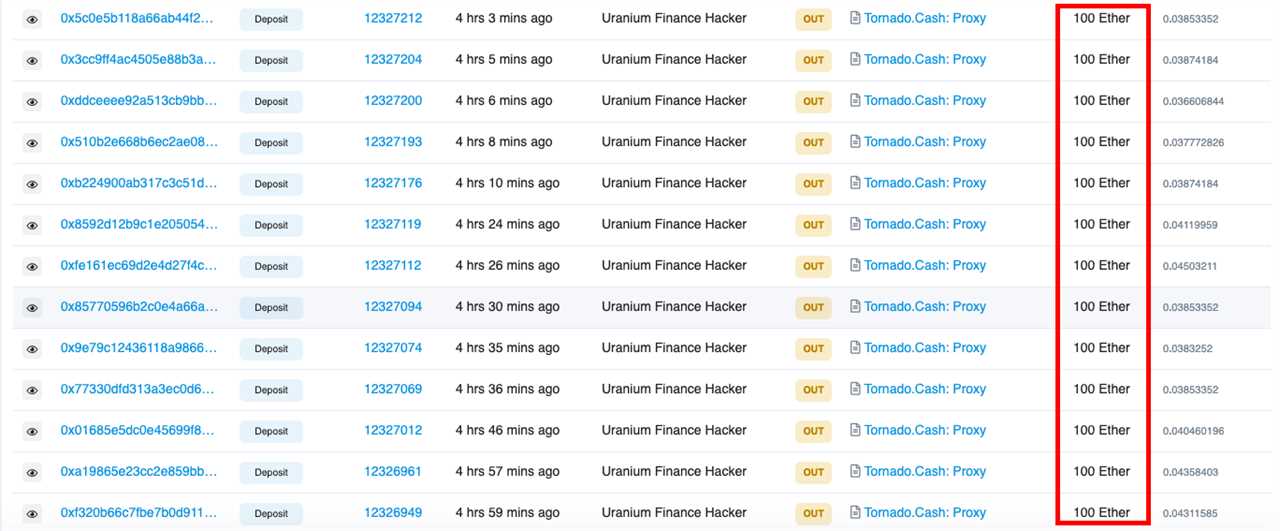
Data from Ethereum chain monitoring service Etherscan shows the funds moving in 100 ETH sums, with the cross-chain decentralized exchange bridge AnySwap used to migrate funds from BSC to the Ethereum network.
According to Uranium, the project has reached out to the Binance security team to prevent the hacker from moving more funds out of the BSC ecosystem.
Binance did not immediately respond to Cointelegraph’s request for comment. A spokesperson for Uranium revealed that the bug was yet to be patched and that users have been advised to stop providing liquidity on the project and to cash out their funds.
The team also created a Telegram group for victims of the hack while promising to provide updates on the progress being made to recover the stolen funds.
Wednesday’s hack is the second attack on the Uranium project in quick succession. Earlier in April, hackers exploited one of the platform’s pools, stealing about $1.3 million worth of BUSD and BNB.
Indeed, the incident led to the first migration to v2 less than two weeks ago. In a previous announcement, the Uranium developer team said that multiple entities had audited its v2 contracts and that it had learned from its previous mistakes.
Meanwhile, speculation is rife as to whether the attack was an inside job, given the sudden decision to engineer another version upgrade barely 11 days after completing the v2 migration.
Today @UraniumFinance got rekt. The Uranium devs had just deployed v2 of their contracts, and 11 days later they asked everyone to migrate to v2.1. Pretty odd timing for an upgrade, right?
— Kyle "1B TVL" Kistner | Fulcrum | bZx (@BeTheb0x) April 28, 2021
Here's how the bug worked. ⬇️
Hacks associated with smart contract bugs are commonplace within the decentralized finance arena even for fully audited projects — as was the case with MonsterSlayer Finance earlier in April. Back in March, Meerkat, a Yearn.finance clone on the BSC, reportedly “exit-scammed” its users, stealing $31 million in the process.
Days later, the project’s developer team revealed the alleged “rug pull” was a test while outlining plans to return the funds. TurtleDex, another BSC-based project, also exit-scammed shortly after its launch, draining over 9,000 BNB tokens raised during the pre-sale.
Title: $50M reportedly stolen from BSC-based Uranium Finance
Sourced From: cointelegraph.com/news/50m-reportedly-stolen-from-bsc-based-uranium-finance
Published Date: Wed, 28 Apr 2021 12:03:03 +0100
Did you miss our previous article...
https://trendinginthenews.com/crypto-currency/former-govt-official-blames-crypto-mining-for-energy-crisis-in-kyrgyzstan






