Lazarus Group Unleashes "KANDYKORN" Malware
A recent report from Elastic Security Labs reveals that the notorious Lazarus Group has deployed a new form of malware in an attempt to compromise a crypto exchange. The malware, dubbed "KANDYKORN," was used alongside a loader program called "SUGARLOAD." These new tools allowed the attackers to bypass traditional malware detection systems, posing a significant threat to the targeted exchange.
Impersonation and Discord Contact
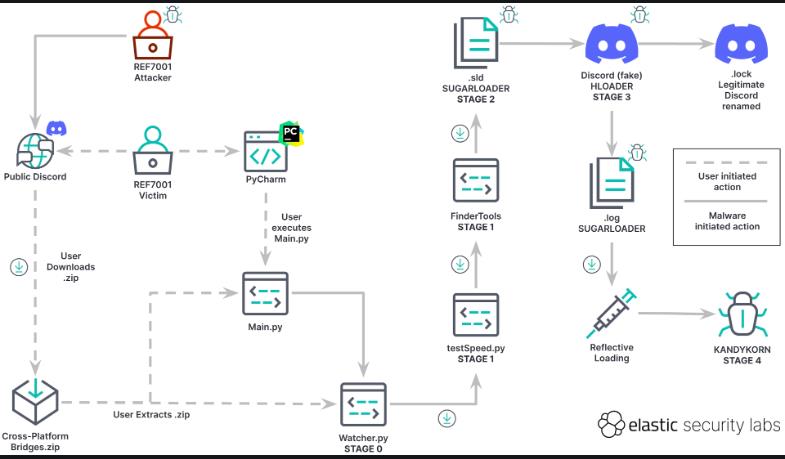
The attack began with Lazarus members posing as blockchain engineers and reaching out to engineers from the crypto exchange via Discord. The attackers claimed to have developed a highly profitable arbitrage bot that could exploit price discrepancies across different exchanges. By establishing trust and offering a seemingly valuable tool, the attackers convinced the engineers to download the malicious program.
Malware Concealed as Arbitrage Bot
The malware was disguised as an arbitrage bot, with files in the program's ZIP folder given innocuous names like "config.py" and "pricetable.py." Once the engineers ran the program, it executed a file called "Main.py," which ran several ordinary programs alongside a malicious file named "Watcher.py." This file established a connection to a remote Google Drive account and downloaded content to another file named "testSpeed.py," which was later deleted to cover the attackers' tracks.
Obfuscated "SUGARLOADER" and Remote Server Connection
The malicious program then executed a file called "SUGARLOADER," which had been obfuscated using a "binary packer." This technique allowed the loader to bypass most malware detection systems. However, Elastic was able to discover it by halting the program after initialization and snapshotting its virtual memory. Once "SUGARLOADER" was downloaded, it connected to a remote server and downloaded the main malware, "KANDYKORN," directly into the victim's device memory.
Continuous Threat and Ongoing Attacks
Elastic believes that the attack occurred in April 2023 but warns that the threat is still active. The tools and techniques used by Lazarus Group are continuously evolving, making it a persistent and dangerous threat to crypto exchanges and their users.
Rash of Attacks on Crypto Exchanges
In 2023, centralized crypto exchanges and apps experienced numerous attacks. Platforms such as Alphapo, CoinsPaid, Atomic Wallet, Coinex, and Stake fell victim to these attacks, with private keys being stolen and customers' cryptocurrency being transferred to the attackers' addresses. The Lazarus Group has been implicated in several of these attacks, including the Coinex hack and the Stake attack, according to the US Federal Bureau of Investigation (FBI).
Did you miss our previous article...
https://trendinginthenews.com/crypto-currency/bitgo-expands-regulatory-compliance-in-germany-with-cryptocurrency-license






