
What are routing attacks?
Routing attacks are deliberate attempts by users to exploit weaknesses in the routing system of the Lightning Network for personal gain. These attacks can affect the network's effectiveness and pose financial risks for users.
How do routing attacks work?
Routing attacks involve tactics such as imposing high routing fees, spreading false information, diverting payments, and conducting probing attacks. These actions can disrupt the network's operations, compromise user privacy, and reduce the network's dependability and usability.
Common routing attacks in the Lightning Network
There are several types of routing attacks in the Lightning Network:
- Routing fee sniping: Setting excessive fees to discourage users from routing through specific channels.
- Probabilistic payment fraud: Pretending a payment was unsuccessful to discourage the use of specific routes or channels.
- Channel jamming attacks: Tying up the liquidity in a channel to render it unavailable to authorized users.
- Balance manipulation: Creating imbalanced channels to disrupt the network's operations.
- Route flapping: Modifying channel restrictions or fee structures to hinder effective routing.
- Sybil attacks: Setting up multiple fictitious nodes to deceive routing algorithms and carry out attacks.
- Onion routing attacks: De-anonymizing transactions by examining routing data.
How to identify routing attacks in the Lightning Network
Identifying routing attacks can be challenging, but tools for network surveillance, watchtowers, route selection, and node behavior analysis can help detect malicious behavior. Active participation in the Lightning Network community and studying previous attacks can also improve one's ability to recognize routing threats.
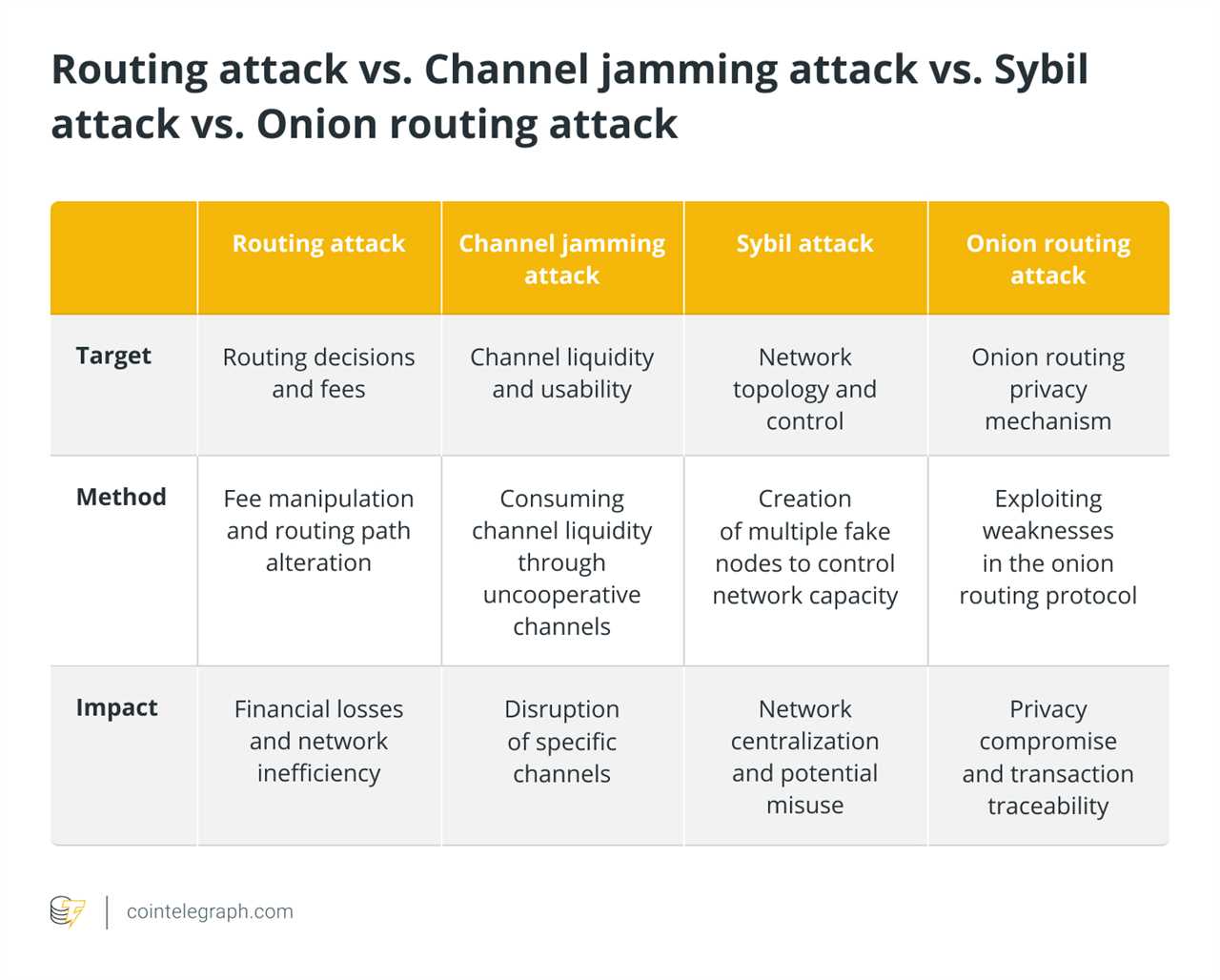
Is channel jamming the same as the routing attack?
Channel jamming is a type of routing attack, but routing attacks encompass a broader range of malicious strategies. Channel jamming involves flooding a specific channel with unsuccessful payments to disrupt its operations, while routing attacks include various tactics to manipulate payment routing and jeopardize network security.
How to avoid routing attacks in the Lightning Network
To protect against routing attacks, users can:
- Choose trusted nodes as routing intermediaries.
- Diversify routing pathways by using multiple channels and nodes.
- Monitor channel activity regularly for anomalies or suspicious behavior.
- Stay updated with the latest Lightning Network software to benefit from security patches and upgrades.
By implementing these strategies, users can strengthen their defenses against routing attacks and promote a more secure environment for Lightning Network transactions.
How to mitigate the security risks associated with crypto payments
In addition to protecting against routing attacks, it is important to mitigate security risks associated with crypto payments. Stay informed about the latest security practices, use hardware wallets, and be cautious of phishing attempts and suspicious websites.
Collect this article as an NFT to preserve this moment in history and show your support for independent journalism in the crypto space.
Did you miss our previous article...
https://trendinginthenews.com/crypto-currency/deutsche-bank-teams-up-with-taurus-for-global-crypto-custody-services






